README.md
1# Routinator
2
3[](https://github.com/NLnetLabs/routinator/actions?query=workflow%3Aci)
4[](https://nlnetlabs.nl/packages/)
5[](https://hub.docker.com/r/nlnetlabs/routinator)
6
7[](https://crates.io/crates/routinator)
8[](https://routinator.readthedocs.io/en/stable/?badge=stable)
9[](https://discord.gg/8dvKB5Ykhy)
10[](https://open.spotify.com/user/alex.band/playlist/1DkYwN4e4tq73LGAeUykA1?si=AXNn9GkpQ4a-q5skG1yiYQ)
11[](https://twitter.com/routinator3000)
12
13<img align="right" src="https://www.nlnetlabs.nl/static/logos/Routinator/Routinator_Avatar_Realistic.svg" height="150">
14
15Introducing ‘Routinator 3000,’ lightweight RPKI relying party software written
16in Rust. Routinator is a full featured software package that runs as a service
17which periodically downloads and verifies RPKI data. The built-in HTTP server
18offers a user interface and API endpoints for various file formats, as
19well as logging, status and Prometheus metrics.
20
21Routinator has a built-in an RTR server allowing routers supporting route origin
22validation (ROV) to connect to it to fetch verified RPKI data. Note that if you
23would like to run the RTR server as a separate daemon, for example because you
24want to centralise validation and distribute processed data to various locations
25where routers can connect, then NLnet Labs provides
26[RTRTR](https://www.nlnetlabs.nl/projects/rpki/rtrtr/).
27
28If you have feedback, we would love to hear from you. Don’t hesitate to [create
29an issue on Github](https://github.com/NLnetLabs/routinator/issues/new) or post
30a message on our [RPKI mailing
31list](https://lists.nlnetlabs.nl/mailman/listinfo/rpki) or [Discord
32server](https://discord.gg/8dvKB5Ykhy). You can learn more by reading the
33[Routinator documentation](https://routinator.docs.nlnetlabs.nl/) and the
34[RPKI technology documentation](https://rpki.readthedocs.io/) on Read the Docs.
35
36## Quick Start with Binary Packages
37
38On the NLnet Labs software package repository we provide Routinator packages for
39amd64/x86_64 architectures running Debian and Ubuntu, as well as Red Hat
40Enterprise Linux and CentOS.
41
42### Installing on Debian/Ubuntu
43
44Add the line below that corresponds to your operating system to your
45`/etc/apt/sources.list` or `/etc/apt/sources.list.d/`
46
47```bash
48deb [arch=amd64] https://packages.nlnetlabs.nl/linux/debian/ stretch main
49deb [arch=amd64] https://packages.nlnetlabs.nl/linux/debian/ buster main
50deb [arch=amd64] https://packages.nlnetlabs.nl/linux/debian/ bullseye main
51deb [arch=amd64] https://packages.nlnetlabs.nl/linux/ubuntu/ xenial main
52deb [arch=amd64] https://packages.nlnetlabs.nl/linux/ubuntu/ bionic main
53deb [arch=amd64] https://packages.nlnetlabs.nl/linux/ubuntu/ focal main
54```
55
56Then run the following commands to add the public key and update the repository
57list
58
59```bash
60wget -qO- https://packages.nlnetlabs.nl/aptkey.asc | sudo apt-key add -
61sudo apt update
62```
63
64You can then install Routinator by running this command
65
66```bash
67sudo apt install routinator
68```
69
70### Installing on RHEL/CentOS
71
72Create a file named `/etc/yum.repos.d/nlnetlabs.repo`, enter this configuration
73and save it:
74
75```bash
76[nlnetlabs]
77name=NLnet Labs
78baseurl=https://packages.nlnetlabs.nl/linux/centos/$releasever/main/$basearch
79enabled=1
80```
81Then run the following command to add the public key
82
83```bash
84sudo rpm --import https://packages.nlnetlabs.nl/aptkey.asc
85```
86
87You can then install Routinator by running this command
88
89```bash
90sudo yum install -y routinator
91```
92
93### Setting up Routinator
94
95Initialise, enable and start Routinator by running these commands. Note that
96`routinator-init` is slightly different than the command used with Cargo.
97
98```bash
99sudo routinator-init
100# Follow instructions provided
101sudo systemctl enable --now routinator
102```
103
104By default, Routinator will start the RTR server on port 3323 and the HTTP
105server on port 8323. These, and other values can be changed in the
106configuration file located in `/etc/routinator/routinator.conf`. You can check
107the status of Routinator with `sudo systemctl status routinator` and view the
108logs with `sudo journalctl --unit=routinator`.
109
110## Quick Start with Docker
111
112Due to the impracticality of complying with the ARIN TAL distribution terms
113in an unsupervised Docker environment, prior to launching the container it
114is necessary to first review and agree to the
115[ARIN Relying Party Agreement](https://www.arin.net/resources/rpki/tal.html).
116If you agree to the terms, you can let the Routinator Docker image install
117the TALs into a mounted volume that is later reused for the server.
118
119```bash
120# Create a Docker volume to persist TALs in
121sudo docker volume create routinator-tals
122# Review the ARIN terms
123# Run a disposable container to install TALs
124sudo docker run --rm -v routinator-tals:/home/routinator/.rpki-cache/tals \
125 nlnetlabs/routinator init -f --accept-arin-rpa
126# Launch the final detached container named 'routinator' exposing RTR on
127# port 3323 and HTTP on port 9556
128sudo docker run -d --restart=unless-stopped --name routinator -p 3323:3323 \
129 -p 9556:9556 -v routinator-tals:/home/routinator/.rpki-cache/tals \
130 nlnetlabs/routinator
131```
132
133For additional isolation, Routinator container is known to successfully run
134under [gVisor](https://gvisor.dev/).
135
136## Quick Start with Cargo
137
138Assuming you have a newly installed Debian or Ubuntu machine, you will need to
139install rsync, the C toolchain and Rust. You can then install Routinator and
140start it up as an RTR server listening on 127.0.0.1 port 3323 and HTTP on
141port 8323.
142
143```bash
144apt install curl rsync build-essential
145curl --proto '=https' --tlsv1.2 -sSf https://sh.rustup.rs | sh
146source ~/.cargo/env
147cargo install --locked routinator
148routinator init
149# Follow instructions provided
150routinator server --rtr 127.0.0.1:3323 --http 127.0.0.1:8323
151```
152
153If you have an older version of Rust and Routinator, you can update using
154
155```bash
156rustup update
157cargo install --locked --force routinator
158```
159
160Routinator 0.7.1 and newer are shipped with updated Trust Anchor Locators
161(TALs). Once you have upgraded from an older version of Routinator, make sure
162to install the new TALs using
163
164```
165routinator init --force
166```
167
168## RPKI
169
170The Resource Public Key Infrastructure provides cryptographically signed
171statements about the association of Internet routing resources. In
172particular, it allows the legitimate holder of an IP prefix to state which
173Autonomous Systems are authorised to originate it in BGP.
174
175All of these statements are published in a distributed repository.
176Routinator will collect these statements into a local copy, verify
177their signatures, and construct a list of associations between IP address
178prefixes and AS numbers. It provides this information to routers supporting
179route origin validation (ROV) or can output it in a number of useful formats.
180
181## System Requirements
182
183Routinator is designed to be lean and is capable of running on minimalist
184hardware, such as a Raspberry Pi. Running it on a system with 1GB of
185available RAM and 1GB of available disk space will give the global RPKI
186data set enough room to grow for the foreseeable future.
187
188As new RPKI repositories can emerge in any IP address range and on any domain
189name, outbound traffic must not be blocked based on IP or DNS in any way.
190Routinator only needs to establish outbound connections via HTTPS and rsync, on
191ports 443 and 873, respectively.
192
193## Getting Started
194
195There’s two things you need for Routinator: rsync and Rust and a C toolc…
196There are three things you need for Routinator: rsync, a C toolchain and
197Rust. You need rsync because some RPKI repositories currently still use this
198as its means of distribution. Some of the cryptographic primitives
199used by the Routinator require a C toolchain, so you need that, too. You
200need Rust because that’s what Routinator has been written in.
201
202### rsync
203
204Currently, Routinator requires the `rsync` executable to be in your path.
205We are not quite sure which particular version you need at the very least,
206but whatever is being shipped with current Linux and \*BSD distributions
207and macOS should be fine.
208
209On Windows, Routinator requires the `rsync` version that comes with
210[Cygwin](https://www.cygwin.com/) – make sure to select rsync during the
211installation phase. And yes, Routinator totally works on Windows, too.
212
213If you don’t have rsync, please head to http://rsync.samba.org/
214
215### C Toolchain
216
217Some of the libraries Routinator depends on require a C toolchain to be present.
218Your system probably has some easy way to install the minimum set of packages to
219build from C sources. For example, `apt install build-essential` will install
220everything you need on Debian and Ubuntu.
221
222If you are unsure, try to run `cc` on a command line and if there’s a complaint
223about missing input files, you are probably good to go.
224
225On some older systems, the toolchain may not be up-to-date. We are collecting
226information as it comes up in a [separate document](doc/misc.md). One such
227instance is [CentOS 6](doc/misc.md#building-on-centos-6).
228
229### Rust
230
231The Rust compiler runs on, and compiles to, a great number of platforms. The
232official [Rust Platform
233Support](https://doc.rust-lang.org/nightly/rustc/platform-support.html) page
234provides an overview of the various platforms and support levels.
235
236While some system distributions include Rust as system packages, Routinator
237relies on a relatively new version of Rust, currently 1.47 or newer. We
238therefore suggest to use the canonical Rust installation via a tool called
239`rustup`.
240
241To install `rustup` and Rust, simply do
242
243```bash
244curl --proto '=https' --tlsv1.2 -sSf https://sh.rustup.rs | sh
245```
246
247or, alternatively, get the file, have a look and then run it manually. Follow
248the instructions to get `rustup` and `cargo`, the Rust build tool, into your
249path.
250
251You can update your Rust installation later by simply running
252
253```bash
254rustup update
255```
256
257To get started you need Cargo's bin directory (`$HOME/.cargo/bin`) in your PATH
258environment variable. To configure your current shell, run
259
260```bash
261source $HOME/.cargo/env
262```
263
264## Building
265
266The easiest way to get Routinator is to leave it to `cargo` by saying
267
268```bash
269cargo install --locked routinator
270```
271
272If you want to try the main branch from the repository instead of a release
273version, you can run
274
275```bash
276cargo install --locked --git https://github.com/NLnetLabs/routinator.git --branch main
277```
278
279If you want to update an installed version, you run the same command but add the
280`-f` flag (a.k.a. `--force`) to approve overwriting the installed version.
281
282The command will build Routinator and install it in the same directory that
283cargo itself lives in (likely `$HOME/.cargo/bin`). Which means Routinator will
284be in your path, too.
285
286## Using native TLS instead of Rustls
287
288Routinator by default uses [Rustls](https://github.com/ctz/rustls) which in
289most cases is fine. However, if needed you can instead use your system native
290TLS implementation with Routinator like so:
291
292**Cargo:**
293
294Build Routinator with the `native-tls` feature enabled
295
296```bash
297git clone --branch vX.Y.Z --depth 1 https://github.com/NLnetLabs/routinator.git
298cd routinator
299cargo build --release --features socks,native-tls
300```
301
302**Docker:**
303
304Specify a `native-tls` image tag when running the container
305
306```bash
307sudo docker run -d --restart=unless-stopped --name routinator -p 3323:3323 \
308 -p 9556:9556 -v routinator-tals:/home/routinator/.rpki-cache/tals \
309 nlnetlabs/routinator:native-tls
310```
311
312## Running
313
314All functions of Routinator are accessible on the command line via subcommands.
315
316The first thing you need to do before running Routinator is prepare its working
317environment via the command
318
319```bash
320routinator init
321```
322
323This will prepare both the directory for the local RPKI cache as well as the TAL
324directory. By default both directories will be located under
325`$HOME/.rpki-cache`, but you can change their locations via command line
326options.
327
328TALs provide hints for the trust anchor certificates to be used both to discover
329and validate all RPKI content. The five TALs that are necessary for RPKI are
330bundled with Routinator and installed by the `routinator init` command.
331
332However, the one from the North American RIR ARIN requires you to agree to their
333Relying Party Agreement before you can use it. Running the `routinator init`
334command will provide you with instructions where to find the agreement and how
335to express your acceptance of its terms.
336
337Some RIRs and third parties also provide separate TALs for testing purposes,
338allowing operators to gain experience with using RPKI in a safe environment.
339Both the production and testbed TALs are bundled with Routinator and can be
340installed with the `init` command. To get an overview of all available TALs
341use the `--list-tals` option
342
343Once you have successfully prepared the working environment, your can run
344Routinator in one of two possible modes: printing the list of valid route
345origins, also known as _validated ROA payloads_ or VRPs, or providing the
346service for routers and other clients to access this list via HTTP or a
347dedicated protocol known as RPKI-to-Router protocol, or RTR.
348
349To have Routinator print the list, you say
350
351```bash
352routinator vrps
353```
354
355When you first run this command, Routinator will download the entire RPKI
356repository to your machine, which will take a while. Later, Routinator only
357needs to check for changes so subsequent runs will be quicker. Once it has
358gathered all data, it will verify it and produce a long list of AS Numbers,
359IP prefixes and their maximum length.
360
361Information about additional command line arguments is available via the `-h`
362option or you can look at the more detailed man page via the `man` sub-command
363
364```bash
365routinator man
366```
367
368The man page is also available online in the
369[documentation](https://routinator.docs.nlnetlabs.nl/en/stable/manual-page.html).
370
371## Feeding a Router with RPKI-RTR
372
373Routinator supports RPKI-RTR as specified in RFC 8210 as well as the older
374version from RFC 6810. It will act as an RTR server if you start it with
375the `routinator server` command.
376
377You can specify the address(es) to listen on via the `--rtr` option. If you
378don't, it will still start but not listen on anything. This may seem a bit odd,
379but this way, you can keep your local repository copy up-to-date for faster use
380of the `routinator vrps` command.
381
382So, in order to run Routinator as an RTR server listening on port 3323 on
383both 192.0.2.13 and 2001:0DB8::13, run
384
385```bash
386routinator server --rtr 192.0.2.13:3323 --rtr [2001:0DB8::13]:3323
387```
388
389By default, the repository will be updated and re-verified every ten minutes.
390You can change this via the `--refresh` option and specify the interval between
391runs in seconds. That is, if you rather have Routinator verify every fifteen
392minutes, the above command becomes
393
394```bash
395routinator server --rtr 192.0.2.13:3323 --rtr [2001:0DB8::13]:3323 --refresh=900
396```
397
398## Secure Transports for RPKI-RTR
399
400[RFC6810](https://tools.ietf.org/html/rfc6810#page-17) defines a number of
401secure transports for RPKI-RTR that can be used for communication between a
402router and RPKI relying party software.
403
404Documentation on configuring secure transports with Routinator can be found
405[here](doc/transports.md).
406
407## Configuration Files
408
409Routinator can take its configuration from a file, too. You can specify such a
410configuration file via the `-c` option. If you don’t, Routinator will check if
411there is a file `$HOME/.routinator.conf` and if it exists, use it. If it doesn’t
412exist and there is no `-c` option, default values are used.
413
414The configuration file is a TOML file. Its entries are named similarly to the
415command line options. Details about the available entries and there meaning can
416be found in the [manual
417page](https://routinator.docs.nlnetlabs.nl/en/stable/manual-page.html#configuration-file).
418In addition, a complete sample configuration file showing all the default values
419can be found in the repository at
420[etc/routinator.conf](https://github.com/NLnetLabs/routinator/blob/main/etc/routinator.conf.example).
421
422## Local Exceptions
423
424If you would like to add exceptions to the validated RPKI data in the form of
425local filters and additions, you can specify this in a file using JSON notation
426according to the [SLURM](https://tools.ietf.org/html/rfc8416) standard. You can
427find two example files in the repository at `/test/slurm`. Use the `-x` option
428to refer to your file with local exceptions.
429
430Routinator will re-read that file on every validation run, so you can
431simply update the file whenever your exceptions change.
432
433## Monitoring
434
435Monitoring a Routinator instance is possible by enabling the integrated
436[Prometheus](https://prometheus.io/) exporter using the `--http`
437configuration option or command line parameter.
438
439Port [9556](https://github.com/prometheus/prometheus/wiki/Default-port-allocations)
440is allocated for this use. A Routinator instance with monitoring on this
441port can be launched using
442
443```bash
444routinator server --rtr 192.0.2.13:3323 --rtr [2001:0DB8::13]:3323 --http 192.0.2.13:9556
445```
446
447A [sample Grafana dashboard](https://grafana.com/grafana/dashboards/11922) is
448available to get started.
449
450## User Interface
451
452The [user interface](https://routinator.docs.nlnetlabs.nl/en/stable/user-interface.html)
453displays statistics from the last validation run Routinator has performed.
454It can also be used to verify the RPKI origin validation status of an AS
455Number and IP Prefix combination.
456
457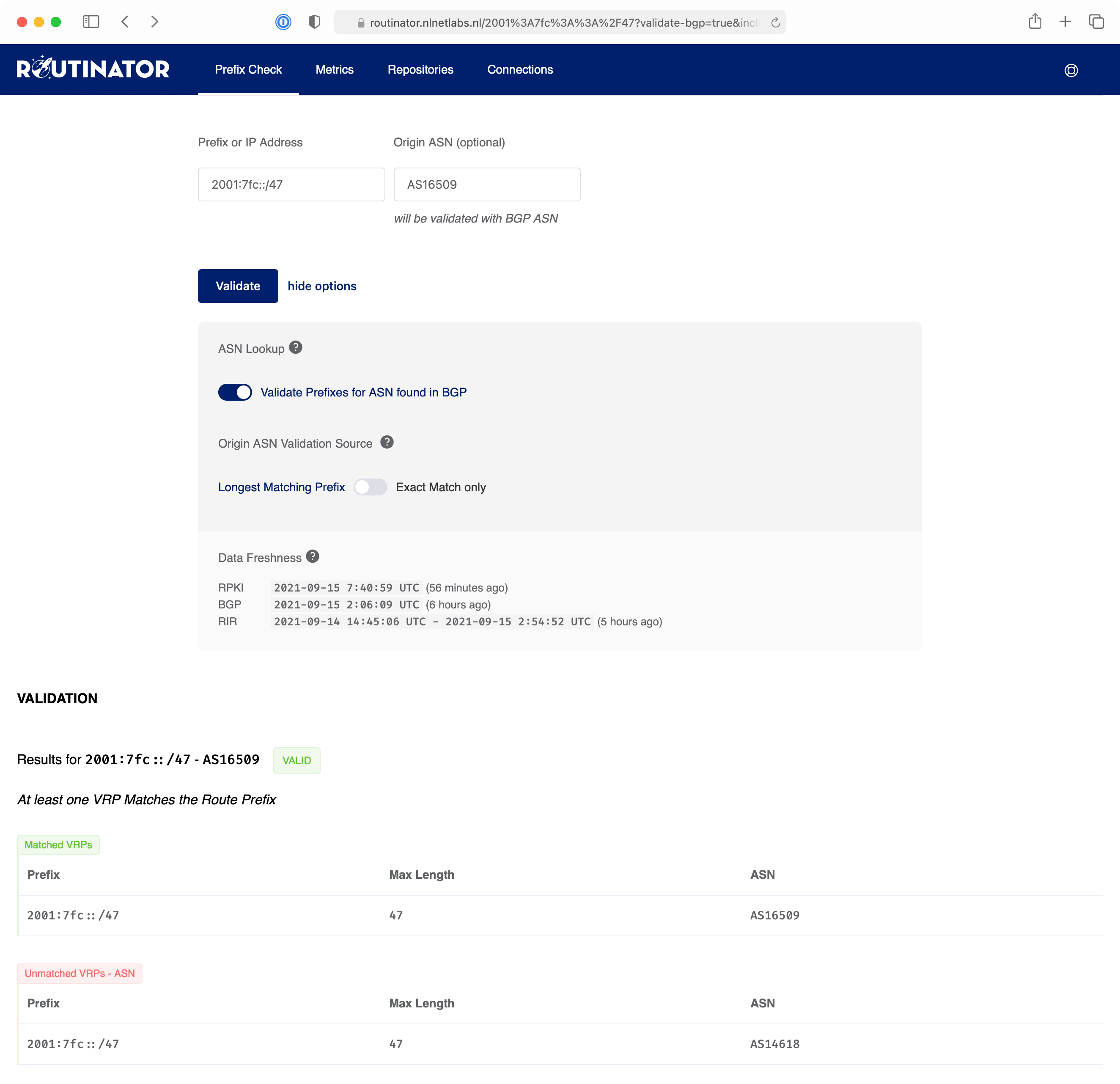
458