README.md
1# The Vanguards Onion Service Addon
2
3[](https://travis-ci.org/mikeperry-tor/vanguards) [](https://coveralls.io/github/mikeperry-tor/vanguards?branch=master)
4
5Even after deployment of the [new v3 onion service
6protocol](https://gitweb.torproject.org/torspec.git/tree/proposals/224-rend-spec-ng.txt),
7the attacks facing onion services are wide-ranging, and still require
8more extensive modifications to fix in Tor-core itself.
9
10Because of this, we have decided to rapid-prototype these defenses in a
11controller addon in order to make them available ahead of their official
12Tor-core release, for onion services that require high security as soon as
13possible.
14
15For details about the defenses themselves, please see
16[README\_TECHNICAL.md](https://github.com/mikeperry-tor/vanguards/blob/master/README_TECHNICAL.md).
17
18For additional security information, please see
19[README\_SECURITY.md](https://github.com/mikeperry-tor/vanguards/blob/master/README_SECURITY.md).
20
21# Installation Methods
22
23There are several ways to use this addon. At the moment, the safest is to run
24it directly from git.
25
26Packages for popular UNIX-like systems should be available soon.
27
28## Running this addon directly from git
29
30**This is the safest option to use, since it avoids having pip and/or
31virtualenv download packages from PYPI without verification.**
32
331. Retrieve this repository and optionally verify a signed git version tag.
342. [Install Stem](https://stem.torproject.org/download.html)
353. Run **./src/vanguards.py**
36
37If your control port is on an alternate IP and Port, specify that with
38**--control_host _IP_ --control_port _portnum_**.
39
40If you are using a control socket, specify its full path with
41**--control_socket /path/to/socket**.
42
43Note that **./src/vanguards.py** has several other options under **--help**.
44
45## Using VirtualEnv
46
47**This option tells virtualenv not to download packages, and only downloads
48pip packages with --require-hashes. It should be safe.**
49
50To install Stem and Vanguards into their own python virtualenv, run:
51
52```
53torsocks ./setup.sh
54source vanguardenv/bin/activate
55vanguards
56```
57
58If you do not want your environment to be in the vanguardenv subdirectory, you
59can specify a different directory as an argument to **setup.sh**.
60
61## Pip
62
63This project is also listed on the Python Package Index. To install the
64latest release via pip **without any verification**, do:
65
66```
67torsocks pip install vanguards
68```
69
70# How to use the addon
71
72## Configuration
73
74All of the subsystems of this addon can be tuned via a configuration file.
75Check out this documented [example configuration file](https://github.com/mikeperry-tor/vanguards/blob/master/vanguards-example.conf) for more information.
76
77Configuration files can be specified on the command line. The default is to
78read **vanguards.conf** from the current working directory. If the environment
79variable **$VANGUARDS\_CONFIG** is set, the config file will be read from the
80file specified in that variable.
81
82## Onion service use
83
84This addon is primarily intended for onion service operators. To use it,
85set up your onion service to expose a control port listener using the
86ControlPort or ControlSocket torrc directives:
87
88```
89ControlPort 9099 # or ControlSocket /path/to/socket
90CookieAuthentication 1
91DataDirectory /path/to/tor/datadir
92```
93
94and then run:
95
96```
97vanguards --control\_port=9099 # (or --control\_socket /path/to/socket).
98```
99
100## Client use
101
102It is also possible to use the vanguards addon as a regular Tor client with
103Tor Browser or with Onionshare.
104
105To use it with Tor Browser, all you have to do is start Tor Browser, and then run:
106```
107 ./src/vanguards.py --control_port 9151
108```
109
110To use it with Onionshare, set up your Tor to expose a control port and attach
111both onionshare and the vanguards addon to it.
112
113## Performance Tuning
114
115For very high traffic onion services, we recommend using
116[PyPy](https://pypy.org) instead of CPython. PyPy contains a JIT that should
117make this addon run considerably faster.
118
119The easiest way to use PyPy is to do **sudo apt-get install pypy** or
120equivalent before running **./setup.sh** as per above. The setup.sh script will
121then see that pypy is installed, and use it by default in the resulting
122virtualenv.
123
124To switch to pypy after running **setup.sh**, simply remove the vanguardenv
125directory and run **setup.sh** again.
126
127If you want to use pypy outside of a virtualenv, install Stem on your system (use 1.5.4 or earlier, since Stem 1.6.0 is [incompatible with pypy at the moment](https://trac.torproject.org/projects/tor/ticket/26207), and then run the addon directly from the source tree with:
128
129```
130 pypy ./src/vanguards.py
131```
132
133Additionally, you can disable components to reduce processing overhead. Try
134disabling Rendguard first. If that is still insufficient, disable Bandguards.
135
136Vanguards by itself should not require much overhead, but if even that is too
137much, you can run the following once per hour from cron to update your torrc
138with fresh layer2 and layer3 guards:
139
140```
141 pypy ./src/vanguards.py --one_shot_vanguards
142```
143
144# What do the logs mean?
145
146This is an experimental addon with many heuristics that still need tuning.
147Events that represent severe issues are at WARN level. You should
148react to these events. Warns are currently emitted for the following
149conditions:
150
1511. When your service is disconnected from the Tor network, we WARN. Downtime
152can be a side channel signal or a passive information leak,
153and you should ensure your Internet connection is reliable to minimize
154downtime of your service as much as possible.
1552. When a hidden service descriptor circuit sends more than 30KB, we WARN. If this
156happens, it is either a bug, a heavily-modified hidden service descriptor,
157or an actual attack.
1583. When you set ExcludeNodes in Tor to exclude countries, but do not give
159Tor a GeoIP file, we WARN.
1604. If you disable killing circuits in the rendguard component, we WARN when
161use counts for rends are exceeded.
1625. With Tor 0.3.4.10 and above, we WARN upon receipt of any dropped/ignored cell.
163
164Events that are detected by heuristics that still need tuning are at NOTICE
165level. They may be a bug, a false positive, or an actual attack. If in doubt,
166don't panic. Please check the [Github
167issues](https://github.com/mikeperry-tor/vanguards/issues/) to see if any
168known false positives are related to these lines, and if not, consider filing
169an issue. Please redact any relay fingerprints from the messages before
170posting.
171
README_SECURITY.md
1# What other attacks are there against Onion Services?
2
3In addition to the attacks that the vanguards addon mitigates (which are
4documented in
5[README\_TECHNICAL.md](https://github.com/mikeperry-tor/vanguards/blob/master/README_TECHNICAL.md)),
6there are many other attacks on onion services. Most of these attacks are
7theoretical and have not been observed in the wild, but that does not make
8them impossible. The attacks that you are at risk for depends upon who is
9interested in trying to deanonymize you, and what their capabilities are.
10
11To help make this more clear, we're going to first go through the general
12taxonomy of adversaries, along with their capabilities and the types of
13attacks they can perform, in the [Adversaries](#adversaries) section.
14
15In the [What can I do to be safer?](#what-can-i-do-to-be-safer) section, we'll
16give some specific recommendations that will help defend against these
17adversaries.
18
19# Adversaries
20
21Adversaries can be roughly categorized as having one or more of four
22positions: [Client](#adversaries-client), [Network](#adversaries-network),
23[Local](#adversaries-local), or [Global](#adversaries-global).
24
25Adversaries can have more than one position at the same time, and each of
26these positions can be either "**active**", or "**passive**". For brevity, we
27do not make heavy use of the **active/passive** distinction in this document.
28
29The adversary may also have additional outside information or suspicions that
30can help them mount their attacks.
31
32Each of the adversary subsections below starts with a list of capabilities
33that the adversary has, and this list is followed by additional paragraphs
34that describe the specific attacks that provide those capabilities. When
35relevant, we link to our specific mitigation recommendations from each attack
36description paragraph.
37
38We classify each adversary capability using the following action verbs that
39describe the scope of that capability:
40
41 1. **Suspect** - When we say **"suspect"** with respect to a capability, that
42means that the adversary can perform an attack to obtain this information, but
43they will not have high certainty that they are correct. Depending on the
44attack, they may end up suspecting a lot of unrelated Tor clients as a result
45of their attack. These attacks may also fail to suspect the client that is
46actually of interest to them.
47 2. **Confirm** - When we say **"confirm"** with respect to a capability,
48that means that the adversary is able to use an attack to confirm outside
49information, prior suspicion, or speculation with extremely high certainty.
50 3. **Determine** - When we say **"determine"** with respect to a capability, that
51means that the adversary can perform an attack to obtain the described
52information with extremely high certainty in a relatively short amount of
53time, if the conditions for the attack are met.
54
55Attacks that merely allow the adversary to **suspect** information are not
56typically useful, unless there is also an attack that allows the adversary to
57**confirm** that information.
58
59Attacks that allow an adversary to **confirm** information are not useful
60unless the adversary has some prior information or suspicion.
61
62Attacks that **determine** information right away are thus more powerful
63than attacks that **confirm** information, because they do not require any
64prior information or suspicion. They are also more useful to the adversary
65than attacks that allow them to **suspect** information, because they provide
66a very high degree of certainty.
67
68## Adversaries: Client
69
70Client adversaries are those that attack your onion service using nothing more
71than a Tor client and normal internet access.
72
73In addition to nuisances such as DoS attacks, these adversaries can
74perform anonymity attacks that provide the following capabilities:
75
761. **Determine** if a specific onion service is exploitable, and if so, exploit it (possibly learning the IP address).
772. **Determine** if a specific onion service is also listening on a public IP address, by scanning the public internet for it.
783. **Determine** if a specific onion service always goes down at the same time as
79a public Tor relay goes down.
804. **Determine** that a specific onion service is running the vanguards addon.
815. **Suspect** that a specific onion service is using [OnionBalance](https://github.com/DonnchaC/onionbalance).
826. **Suspect** that a specific onion service may be using a particular Guard.
83
84Capabilities #1-3 should be self-explanatory.
85
86For capability #4, the client adversary can **determine** that a specific onion
87service address is running the vanguards addon by observing how that onion
88service behaves. In particular, it can attempt one of the attacks that the
89vanguards addon defends against, and see if the onion service closes circuits
90in response. In these cases, log lines will be emitted by the vanguards addon
91at NOTICE level or above. If you do not want client adversaries to be able to
92easily detect this addon, you can set **close_circuits=False** in
93[vanguards.conf](https://github.com/mikeperry-tor/vanguards/blob/master/vanguards-example.conf).
94However, a network adversary who runs your Guard node can still **determine**
95that you use this addon (see the [network adversary
96section](#adversaries-network) for details).
97
98For capability #5, the client adversary can **suspect** that a specific onion
99service address is running
100[OnionBalance](https://github.com/DonnchaC/onionbalance). This is because the
101onion service descriptors for OnionBalance instances will often contain more
102introduction points than normal, and these introduction points may even be
103split across multiple distinct onion service descriptors. (The client only
104**suspects** this because both of these things can happen in normal onion
105service operation as well). To reduce the ability of the client adversary to
106**suspect** this, set **DISTINCT_DESCRIPTORS=False** and
107**MAX_INTRO_POINTS=7** in your OnionBalance configuration.
108
109For capability #6, the client adversary may be able to **suspect** that a specific
110onion service is using a particular guard by attacking that guard. If that
111guard goes down or becomes slower, they may notice the effect on that onion
112service. This is one of the reasons why the vanguards addon uses two guards in
113a balanced way by default. Additionally, the adversary may be able to flood an
114onion service with traffic to notice spikes in our public relay bandwidth
115statistics at the guard. Setting **circ_max_megabytes** in
116[vanguards.conf](https://github.com/mikeperry-tor/vanguards/blob/master/vanguards-example.conf)
117to an appropriate value for your service can help you detect and mitigate this
118attack.
119
120## Adversaries: Network
121
122Network adversaries are those that run relays in the Tor network, and/or that
123compromise Tor relays. They can also use the network (or a Tor client) to
124inject traffic of their choice (especially against onion services).
125
126The vanguards addon is designed to protect against network adversaries.
127Setting aside the attacks that the vanguards addon defends against (which are
128documented in
129[README\_TECHNICAL.md](https://github.com/mikeperry-tor/vanguards/blob/reamde/README_TECHNICAL.md)),
130network adversaries can still perform attacks that provide the following
131capabilities:
132
1331. **Determine** your Guard relays, if they run one of your Layer2 middle relays.
1342. **Determine** that you are running an onion service that is using the vanguards
135 addon, if they run one of your Guard relays.
1363. **Confirm** that a specific onion service is using their Guard or Layer2 middle
137 relays, if it is.
1384. **Confirm** that a specific onion service is not using their Guard or Layer2
139 middle relays, if it is not.
140
141The vanguards addon is designed to make the network adversary's attacks as
142difficult and unlikely as possible, and to take as long as possible, but they
143can still succeed if you get unlucky. The Tor Project takes these attacks
144seriously, and they are topics of [active
145research](https://blog.torproject.org/tors-open-research-topics-2018-edition),
146but for now, the vanguards addon is the best way we have to defend against
147this adversary class.
148
149For statistics on how long capability #1 takes, please see [our analysis of
150our parameter
151choices](https://github.com/asn-d6/vanguard_simulator/wiki/Optimizing-vanguard-topologies).
152
153For capability #2, if you are using a guard relay run by the network adversary, they can
154**determine** that you are running an onion service that is using the
155vanguards addon through [circuit fingerprinting attacks](https://www.usenix.org/node/190967).
156All of your onion service circuits (which are recognizable via the techniques
157from that paper) will be made to a small set of layer2 vanguard relays. Normal
158onion services (which are also recognizable at the guard relay via these same
159techniques) will make circuits to the entire set of relays in the Tor network.
160This discrepancy allows a malicious guard to determine that you are using the
161vanguards addon.
162
163For capability #3 and #4, the network adversary is able to perform
164**confirmation** attacks to **confirm** that you are or are not using their
165Guard or middle relays via the following mechanisms:
166
1671. Inject special types of traffic at specific times towards your onion service (as was done [by CMU with RELAY_EARLY](https://blog.torproject.org/tor-security-advisory-relay-early-traffic-confirmation-attack), and [shown in the DropMark attack](https://petsymposium.org/2018/files/papers/issue2/popets-2018-0011.pdf)).
1682. Inject large amounts of traffic towards your onion service, and look for these additional traffic patterns on their relays.
1693. Close circuits at their relays, and observe if this causes any of their connections to your onion service to close.
1704. Utilize [cryptographic tagging attacks](https://lists.torproject.org/pipermail/tor-dev/2012-March/003347.html) to mark circuits at their relays, and observe this mark at other relays (such
171as the Rendezvous Point).
172
173The vanguards addon has additional checks to detect activity related to these attacks, as well. Those details are covered in
174[README\_TECHNICAL.md](https://github.com/mikeperry-tor/vanguards/blob/reamde/README_TECHNICAL.md).
175
176## Adversaries: Local
177
178Local adversaries include your WiFi [router
179administrator](https://nakedsecurity.sophos.com/2018/04/18/russias-grizzly-steppe-gunning-for-vulnerable-routers/), ISP, hosting provider, or VPN, as well as the ISP or hosting provider of
180the Tor relays you use to connect to the Tor network, and any other ISPs and
181[routers](https://spectrum.ieee.org/tech-talk/computing/hardware/us-suspicions-of-chinas-huawei-based-partly-on-nsas-own-spy-tricks) along your path to the Tor network.
182
183The local adversary has less surveillance resolution than the network
184adversary, because Tor's TLS encryption prevents it from knowing which of
185your packets belong to which Tor circuit. This means that the local adversary
186cannot perform most of the fingerprinting and related attacks that the network
187adversary can perform.
188
189However, local adversaries still have the following capabilities:
190
1911. **Determine** that you are using the public Tor network.
1922. **Suspect** that your Tor client might be running an unknown onion service.
1933. **Suspect** that your Tor client might be running the vanguards addon (soon to be
194 fixed).
1954. **Confirm** that you are running a specific onion service address, if you are
196 running a specific service that is of interest to them.
197
198For capability #1, local adversaries can **determine** that you are running Tor
199because the list of Tor relays is public, and connections to them are obvious.
200[Using a bridge with your onion service](#the-best-way-to-use-bridges) can
201help mitigate this attack.
202
203For capability #2, local adversaries might **suspect** that your Tor client could
204be an unknown onion service because it exhibits traffic patterns that are
205unlike most other Tor clients. Your connections will stay open all of the
206time, and you will regularly transmit data while other nearby humans are
207asleep, as well as while they are awake. Your traffic will also be
208asymmetrical. While most Tor clients download, you will likely be doing a lot
209of uploading. [Using or running a bridge or Tor
210relay](#Use-Bridges-or-Run-a-Relay-or-Bridge) with your
211Onion Service can help conceal these traffic patterns, especially when [used
212in combination with OnionBalance](#using-onionbalance).
213
214For capability #3, local adversaries might also **suspect** that you could be
215using the vanguards addon, at least until [Proposal
216291](https://gitweb.torproject.org/torspec.git/tree/proposals/291-two-guard-nodes.txt)
217is turned on. This is because you will be using two Guards in a balanced way,
218as opposed to using a second Guard only sometimes (as normal clients do
219today). Proposal 291 is a consensus parameter change. The rest of the Tor
220Project has to agree that this is a good idea, and the change will be
221immediate. I am convinced that worse attacks are possible without this
222consensus parameter change, but discussion and deliberation of all possible
223attacks and all possible future alternatives can take a while. Sometimes
224years. In the meantime, I am still convinced it is safer for onion services to
225use two guards in a balanced way, even if they stand out for doing so.
226
227With capability #2 and #3, the local adversary may **suspect** that you could be
228running an onion service, and maybe even one that wants high security, but
229they will not know which onion service it is.
230
231For capability #4, if the adversary is interested in deanonymizing a small set of
232specific onion service addresses, they can attempt to **confirm** that you are
233running one of these specific services on their local network via a few
234different attack vectors:
235
2361. Block your connection to Tor (or disable your internet connection) to see if any onion services they care about go down.
2372. Send lots of traffic to the onion service to see if you get more traffic on your internet connection.
2383. Kill your TCP connections to see if any of their connections to that onion service close.
2394. If you weren't using vanguards, they can confirm an onion service even
240 easier (see [Proposal 291](https://gitweb.torproject.org/torspec.git/tree/proposals/291-two-guard-nodes.txt) for details).
241
242The first two vectors of this **confirmation** attack can be mitigated by
243[using OnionBalance](#using-onionbalance), and by setting
244**circ_max_megabytes** in your
245[vanguards.conf](https://github.com/mikeperry-tor/vanguards/blob/master/vanguards-example.conf)
246to an appropriate value for your service.
247
248Unfortunately, the third vector is not possible to fully mitigate until Tor
249supports datagram transports and [conflux-style session
250resumption](https://www.cypherpunks.ca/~iang/pubs/conflux-pets.pdf).
251
252However, [monitoring your service closely](#monitor-your-service) for
253connectivity loss can help you detect attempts by the adversary to **confirm**
254your service location. The vanguards addon will emit NOTICE and WARN messages
255related to connectivity loss, and your service will become unreachable.
256
257## Adversaries: Global
258
259A global adversary is an adversary that can observe large portions of the
260internet. [The Five Eyes](https://en.wikipedia.org/wiki/Five_Eyes) and its
261extended versions are the canonical example of this adversary. However,
262adversaries that can compromise a large number of internet routers (such as
263[Russia](https://nakedsecurity.sophos.com/2018/04/18/russias-grizzly-steppe-gunning-for-vulnerable-routers/)
264or
265[China](https://spectrum.ieee.org/tech-talk/computing/hardware/us-suspicions-of-chinas-huawei-based-partly-on-nsas-own-spy-tricks))
266are also in this class.
267
268The global adversary can perform most of the attacks that the local adversary
269can, but everywhere. (It may be significantly more expensive for the global
270adversary to perform **active** attacks than it is for the local adversary to
271do so, but for the most part this degrades their capability only slightly).
272
273The global adversary has the following capabilities:
274
2751. **Determine** a list of most/all IPs that connect to the public Tor network.
2762. **Suspect** which of these IPs might be running onion services.
2773. **Suspect** which of these IPs might be using the vanguards addon (soon to be fixed).
2784. **Suspect** that an IP might be running a specific onion service address, if it is
279 running a specific service that is of interest to them.
280
281The mitigations for these are the same as they are for the local adversary.
282
283This same adversary can theoretically perform additional attacks to attempt to
284deanonymize all Tor traffic all of the time, but [there are
285limits](http://archives.seul.org/or/dev/Sep-2008/msg00016.html) to how well
286those attacks scale. These limits are also the reason that the global
287confirmation attack has been degraded to "**suspect**" for #4.
288
289For capability #4, the global adversary becomes more certain in their
290suspicion if they are able to induce the onion service to transmit
291significantly more traffic than its baseline for a long period of time. Again,
292the mitigations for this are to use [OnionBalance](#using-onionbalance), use
293or run
294[a bridge](#Use-Bridges-or-Run-a-relay-or-Bridge) with your
295onion service, and/or set **circ_max_megabytes** in your
296[vanguards.conf](https://github.com/mikeperry-tor/vanguards/blob/master/vanguards-example.conf)
297to an appropriate value for your service.
298
299
300# What can I do to be safer?
301
302Quite a few things. Using the vanguards addon is a good start, but it is not
303the whole picture.
304
305There are four classes of things you can do to improve your position against
306various attacks:
307
3081. [Have Good Opsec](#have-good-opsec)
3092. [Use Bridges or Run a Relay or Bridge](#use-bridges-or-run-a-relay-or-bridge)
3103. [Configure OnionBalance Correctly](#using-onionbalance)
3114. [Monitor Your Service](#monitor-your-service)
312
313## Have Good Opsec
314
315Before worrying about any of these advanced attacks on the Tor network, you
316should make sure that your onion service is not leaking basic info via the
317application layer, or by allowing connections outside of Tor.
318
319For information about how to do this, you should have a look at the [Riseup Onion Services Best Practices document](https://riseup.net/en/security/network-security/tor/onionservices-best-practices).
320
321## Use Bridges or Run a Relay or Bridge
322
323Tor has only basic defenses against traffic analysis at the moment. We are
324working on more, but in the meantime, using a bridge or running a relay or
325bridge can provide some additional protection against traffic analysis
326performed by local and global adversaries.
327
328Bridges can help conceal the fact that you are connecting to the Tor network.
329If you use a bridge address that is not known to the adversary, both the local
330and global adversaries will have a harder time performing their attacks.
331
332Running a relay or bridge with your service can help the traffic patterns of
333your service blend in with the rest of the Tor network, but this is tricky to
334set up correctly, and you must take additional steps to decorrelate your
335service uptime from your relay uptime.
336
337### The Best Way To Use Bridges
338
339Right now, the best bridge protocol to use is obfs4, because it has additional
340traffic analysis obfuscation techniques that make it harder for the local and
341global adversaries to use bandwidth side channels and other traffic
342characteristics.
343
344To use obfs4, obtain two bridges from
345[bridges.torproject.org](https://bridges.torproject.org/bridges?transport=obfs4)
346and add them to your torrc like so:
347
348```
349UseBridges 1
350Bridge obfs4 85.17.30.79:443 FC259A04A328A07FED1413E9FC6526530D9FD87A cert=RutxZlu8BtyP+y0NX7bAVD41+J/qXNhHUrKjFkRSdiBAhIHIQLhKQ2HxESAKZprn/lR3KA iat-mode=2
351Bridge obfs4 38.229.1.78:80 C8CBDB2464FC9804A69531437BCF2BE31FDD2EE4 cert=Hmyfd2ev46gGY7NoVxA9ngrPF2zCZtzskRTzoWXbxNkzeVnGFPWmrTtILRyqCTjHR+s9dg iat-mode=2
352
353ClientTransportPlugin obfs2,obfs3,obfs4,scramblesuit exec /usr/bin/obfs4proxy
354```
355
356Note the use of the iat-mode=2 parameter. Setting iat-mode=2 (as opposed to
357iat-mode=0 or 1) causes obfs4 to inject traffic timing changes into your
358outgoing traffic, which is exactly the direction you want as a service. The
359bridge itself does not need to have the same setting.
360
361You can get that obfs4proxy binary as a debian package, or from a recent Tor
362Browser version, or [build it from source](https://gitweb.torproject.org/pluggable-transports/obfs4.git/).
363
364### The Best Way to Run Tor Relays Or Bridges With Your Service
365
366Instead of using bridges, another alternative is to use the Tor network itself
367as cover traffic for your service by running a relay or bridge. If your relay
368or bridge is used enough (especially by other onion service client and service
369traffic), this will help obscure your service's traffic.
370
371The seemingly obvious approach would be to use the same Tor process for your
372relay as you use for your onion service. This will accomplish the traffic
373blending on the same TLS connections as relayed Tor traffic. Unfortunately,
374because Tor is single threaded, your onion service activity can still cause
375stalls in the overall network activity of your relay. See
376[Ticket #16585](https://trac.torproject.org/projects/tor/ticket/16585) for the gory
377details. Worse still, if it is the same process, your Tor relay will report
378your onion service history in its read/write statistics, which result in a
379[noticeable asymmetry in these
380statistcis](https://trac.torproject.org/projects/tor/ticket/8742).
381
382However, if you run your Tor relay as a separate process on the same machine
383as your onion service Tor process, but **also** use that relay locally as a
384bridge, your onion service activity will not directly block the relay
385activity, but will still share all of its outbound TLS connections to other
386relays. For this, you would add something like the following to your onion
387service torrc:
388
389```
390UseBridges 1
391Bridge 127.0.0.1:9001 # 9001 is the relay process's OR port.
392```
393
394The story deepens, however. When you do this, **your onion service uptime will
395be strongly correlated to your relay uptime, and both are now very
396easily observable by client adversaries**.
397
398[OnionBalance](#using-onionbalance) is one way to address this (ie: running
399several Tor relays on different machines, each with their own OnionBalance
400Backend Instance).
401
402To look as much like a normal onion service as possible, you should use two
403Tor relays, and each on different machines in different data centers. In this
404way, your traffic will appear as an onion service that is using your two
405guards, and your onion service as a whole won't go down unless both of your
406relays are down.
407
408## Using OnionBalance
409
410[OnionBalance](https://onionbalance.readthedocs.io/en/latest/getting-started.html#architecture)
411can help protect against some forms of traffic analysis and confirmation
412attacks. It does this at the expense of more exposure to a larger number of
413local adversaries, though, and if the adversary can tell that you are using
414OnionBalance, they can counteract many of the benefits.
415
416Despite exposing you to more local adversaries, OnionBalance helps protect
417against local adversaries because they will no longer be able to observe all
418of your onion service traffic, and it is more difficult for them to impact
419your reachability for a reachability confirmation attack.
420
421Additionally, when OnionBalance is used in combination with the addon's
422bandguards component option **circ_max_megabytes**, this can help protect
423against bandwidth confirmation attacks that send high volumes of traffic to
424interesting onion services and watch for any evidence of results on a local
425internet connection.
426
427However, OnionBalance needs some tweaks to avoid giving an advantage to the
428network adversary. Because multiple instances of the vanguards addon do not
429communicate through OnionBalance, each additional instance of the vanguards
430addon will choose different layer2 and layer3 guards. These additional layer2
431and layer3 guards increase the overall exposure to guard discovery attacks. In
432cases where it is just as bad for the adversary to discover any of your onion
433service instances as it is to discover all of them, then obviously each
434additional instance lowers your security a bit.
435
436### How to OnionBalance
437
438To attempt to conceal the fact that you are using OnionBalance, you want your
439OnionBalance service to produce descriptors with similar numbers of
440introduction points as normal services. Normal services typically have between
4413 and 7 introduction points. This means you should set the OnionBalance
442setting **MAX_INTRO_POINTS=7**, and also set **DISTINCT_DESCRIPTORS=False**,
443to prevent it from generating multiple descriptors.
444
445To keep your layer2 and layer3 vanguards in sync between your OnionBalance
446Management Server and the backend instances, first run vanguards on your
447Management Server.
448
449Then, once per hour, copy the **vanguards.state** file from your OnionBalance
450Management Server to each of your Backend Instances, via tor+scp or some other
451secure mechanism. (The UNIX crontab program is a good way to do this copy
452hourly).
453
454When each Backend Instance gets this copied statefile (let's call it
455**mgmt-vanguards.state**), it should run
456```
457 ./src/vanguards.py --one_shot_vanguards --state mgmt-vanguards.state
458```
459
460This will cause the Backend Instance to update its tor settings with the same
461layer2 and layer3 guard information as on the management side. It does not
462matter if your Backend Instances cannot write to their torrc files. The
463settings will still be updated.
464
465Then, to benefit from the other defenses, each Backend Instance should run a
466separate vanguards process with a different state file, but with vanguards
467itself disabled. This is done with something like:
468```
469 ./src/vanguards.py --disable_vanguards --state backend-vanguards.state
470```
471
472These backend instances will then still monitor and react to bandwidth side
473channel attacks and Rendezvous Point overuse, while still using the same
474layer2 and layer3 guards as your Management Server.
475
476## Monitor Your Service
477
478As we discussed above, confirmation attacks can be performed by local and
479global adversaries that block your access to Tor (or kill your Tor
480connections) to **confirm** if this impacts the reachability of a suspect hidden
481service or not. This is a good reason to monitor your onion service reachability very
482closely with monitoring software like [Nagios](https://www.nagios.org/) or
483[Munin](http://munin-monitoring.org/).
484
485If you use OnionBalance, you need to monitor the ability of each of your
486Backend Instances to connect to Tor and receive connections to their unique
487backend onion service addresses. If the adversary **suspects** that you are
488using OnionBalance, they can perform reachability confirmation attacks against
489the specific backend instances, so monitoring their uptime is a wise move.
490
491If you use bridges or run relays, you should monitor their uptime as well, and
492replace them immediately if they go down.
493
494The vanguards addon also emits WARN messages when it detects that you have lost
495connectivity to the Tor network, or when you still have connectivity to the Tor
496network, but you are unable to build circuits. It also emits NOTICE messages
497if any connections were forcibly closed while they had active circuits on them.
498
499You should add the output of the vanguards addon to your monitoring
500infrastructure for this reason (in addition to watching for evidence of
501the other attacks the addon detects).
502
README_TECHNICAL.md
1# What does this addon do?
2
3This addon uses the [Stem Tor control port
4library](https://stem.torproject.org/) to connect to a Tor control port
5listening on port 9051 (or on an alternate user-specified port, or UNIX file
6system socket).
7
8This addon protects against guard discovery and related traffic analysis
9attacks. A guard discovery attack enables an adversary to determine the guard
10node(s) that are in use by a Tor client and/or Tor onion service. Once the
11guard node is known, traffic analysis attacks that can deanonymize an onion
12service (or onion service user) become easier.
13
14The most basic form of this attack is to make many connections to a Tor onion
15service, in order to force it to create circuits until one of the adversary's
16relay is chosen for the middle hop next to the guard. That is possible because
17middle hops for rendezvous circuits are picked from the set of all relays:
18
19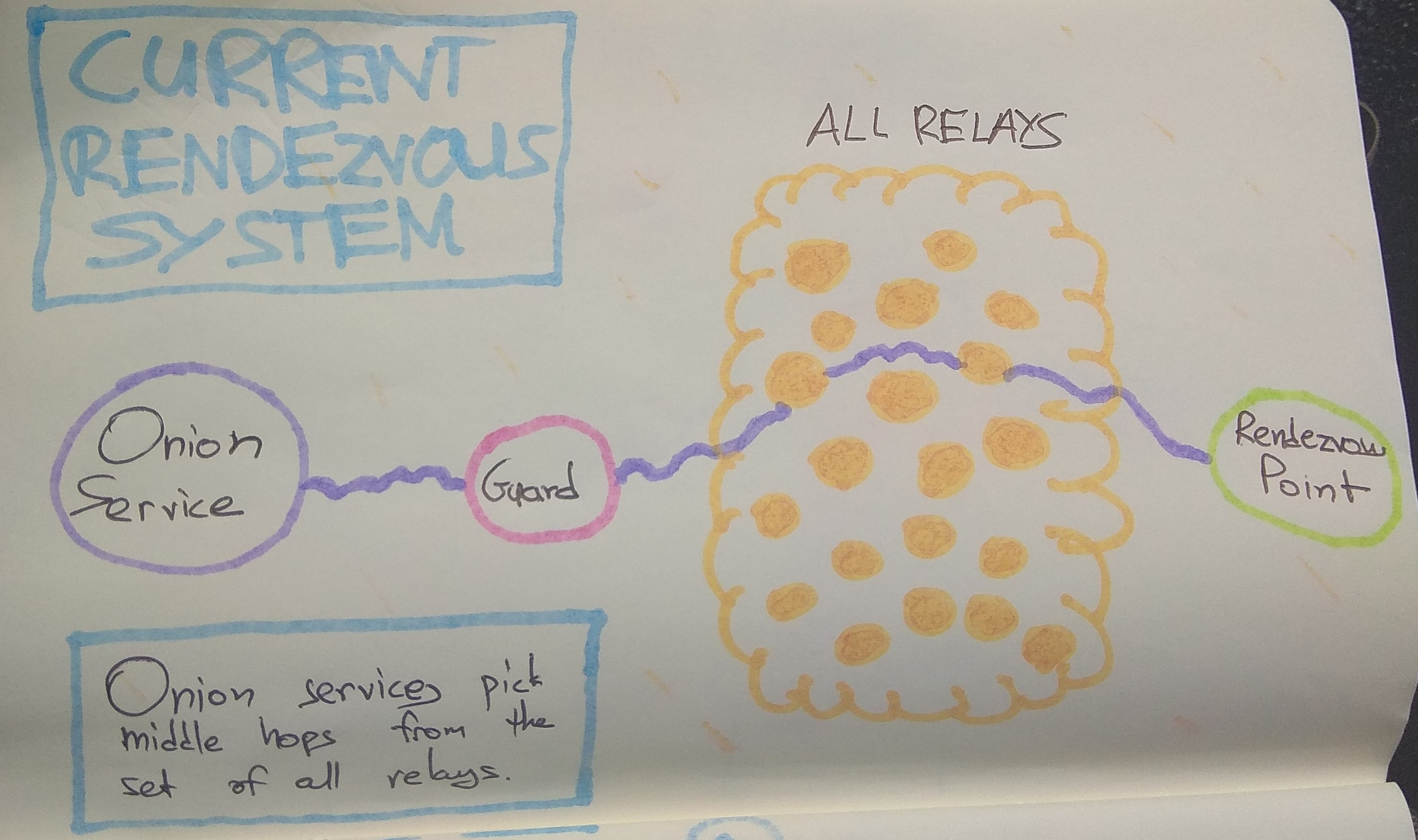
20
21This attack can also be performed against clients, by inducing them to create
22lots of connections to different onion services, by for example, injecting
23lots of onion-hosted images/elements into a page.
24
25A traffic analysis side channel can be used to confirm that the malicious node
26is in fact part of the rendezvous circuit, leading to the discovery of that
27onion service's or client's guard node. From that point, the guard node can be
28compromised, coerced, or surveilled to determine the actual IP address of the
29onion service or client.
30
31To defend against these attacks, this addon has three defense subsystems:
32Vanguards, Rendguard, and Bandguards.
33
34All three subsystems apply to both service-side and client-side onion service
35activity. With Tor v0.3.5.1 and Vanguards v0.3.0 and above, the Bandguards
36subsystem also applies to client traffic that exits the Tor network to the
37normal Internet.
38
39## The Vanguards Subsystem
40
41The Vanguards subsystem uses the [Tor control
42protocol](https://gitweb.torproject.org/torspec.git/tree/control-spec.txt) to
43select nodes from the Tor consensus for use with the torrc options HSLayer2Nodes
44and HSLayer3Nodes.
45
46Each of these options is assigned its own set of nodes, which are rotated
47based on the randomized selection algorithm specified in [the Mesh Vanguards
48Proposal](https://gitweb.torproject.org/torspec.git/tree/proposals/292-mesh-vanguards.txt).
49
50These options ensure that all onion service circuits are restricted to a set
51of second and third layer guards, instead of sampling random ones from the
52whole network every time.
53
54The change to fixed nodes for the second and third layer guards is designed
55to force the adversary to have to run many more nodes, and to execute both an
56active sybil attack, as well as a node compromise attack. In particular, the
57addition of second layer guard nodes means that the adversary goes from being
58able to discover your guard in minutes by running just one middle node, to
59requiring them to sustain the attack for weeks or even months, even if they
60run 5% of the network.
61
62The analysis behind our choice for the number of guards at each layer, and for
63rotation duration parameters is [available on
64GitHub](https://github.com/asn-d6/vanguard_simulator/wiki/Optimizing-vanguard-topologies).
65Here is how our current vanguard 2-3-8 topology looks like:
66
67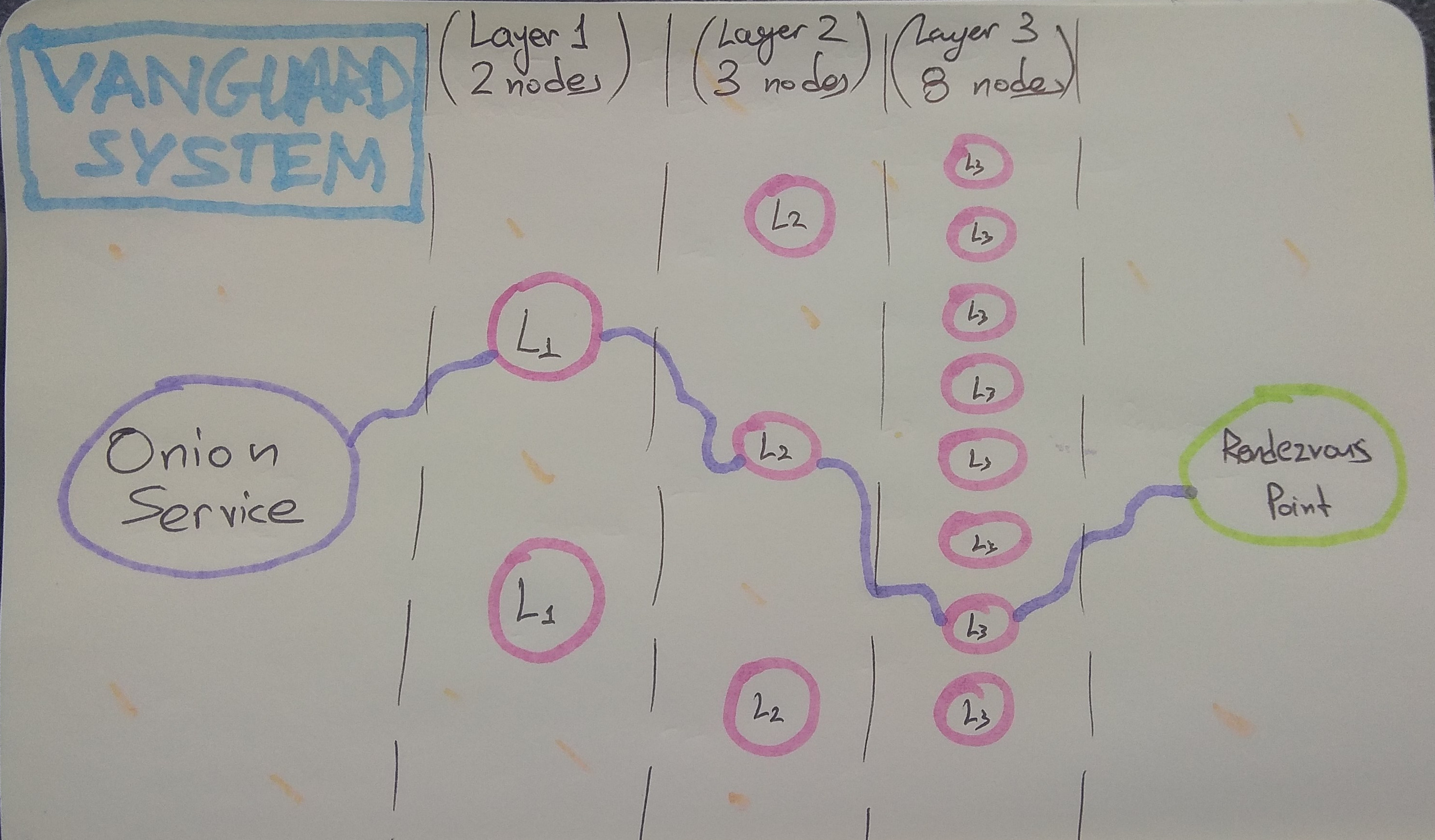
68
69Furthermore, to better protect the identity of these new pinned guard nodes,
70and to avoid linkability of activity, the circuit lengths have been
71altered for rendezvous point circuits, hidden service directory circuits, and
72introduction point circuits. You can see them here (where L1 is the first
73layer guard, L2 is second layer guard, L3 is third layer guard, M is random
74middle):
75
76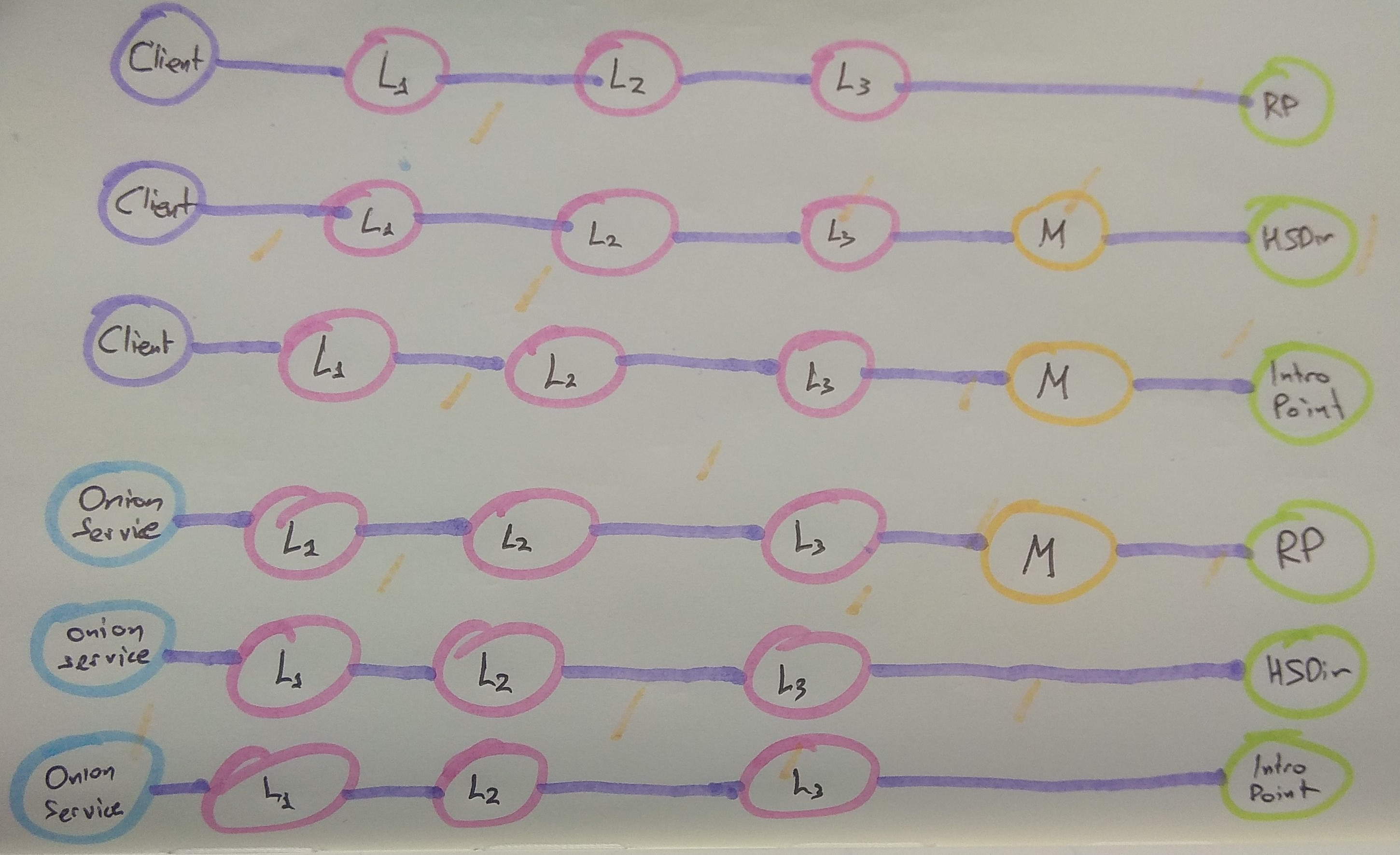
78
79The number of nodes in each of these sets, as well as the ranges on rotation
80times for each set, can be specified as config file parameters. The subsystem
81currently uses 2 entry guards, 3 layer2 guards, and 8 layer3 guards.
82
83High load onion services may consider using 4 layer2 guards by changing the
84**num_layer2_guards** option in the [configuration
85file](https://github.com/mikeperry-tor/vanguards/blob/master/vanguards-example.conf), but going beyond that is not recommended.
86
87## The Rendguard Subsystem
88
89The Rendguard subsystem keeps track of how often various relays appear in the
90rendezvous point position on the service side of an onion service. Since
91rendezvous points are chosen by the client that connects to a service, it
92is possible for clients to [choose malicious, colluding rendezvous
93points](https://www.ieee-security.org/TC/SP2013/papers/4977a080.pdf) to
94help them mount guard discovery and other attacks.
95
96This subsystem emits warnings and optionally closes the circuit when a
97rendezvous point is chosen too often compared to its consensus weight (the
98"too often" limit is set by the **rend_use_max_use_to_bw_ratio** config
99option, which defaults to 5X of a relay's consensus weight).
100
101We assign an aggregate weight of **rend_use_max_consensus_weight_churn**
102(default: 1% of consensus total) for relays that are not in our current
103consensus that are used as rendezvous points. It is valid to use relays that
104are not in the consensus as rendezvous points, and this can happen naturally
105when a client's consensus is from a different time period as the service's
106consensus. To prevent arbitrary computers from being used as rendezvous
107points, we set this bound on the maximum amount of consensus churn, and use
108that to limit all rendezvous requests that are not present in the service's
109consensus.
110
111When rendezvous points are overused and blocked by the addon, the effect is
112that clients get connection refused responses when they attempt to use
113rendezvous points that are already overused. Since the adversary gets to pick
114their rendezvous point, they can trigger these limits at will, and cause
115popular rendezvous points to be blocked by your service. If this happens, you
116can set **rend_use_close_circuits_on_overuse** to false in your configuration
117file. If you do this, rendezvous overuse messages will appear at WARN level,
118but circuits will not be closed.
119
120## The Bandguards Subsystem
121
122The bandguards subsystem performs accounting to watch for signs of bandwidth
123sidechannel attacks on individual onion service circuits as well as exit
124circuits. It then closes circuits that exceed these limits and emits log
125messages. While we expect the default values to be set properly, these limits
126can be tuned through configuration as well. See the [configuration
127file](https://github.com/mikeperry-tor/vanguards/blob/master/vanguards-example.conf)
128for more details.
129
130These limits (along with a reason for checking them) are as follows:
131
1321. ***Dropped Cell Limit***
133
134 Back in 2014, the Tor network [was attacked](https://blog.torproject.org/tor-security-advisory-relay-early-traffic-confirmation-attack) by Carnegie Mellon researchers ([likely on behalf of the FBI)](https://blog.torproject.org/did-fbi-pay-university-attack-tor-users). The attack injected a side channel using a special packet type that could be recognized at both ends of a Tor circuit.
135
136 This side channel was fixed. Unfortunately, there are many other side channels available that allow an adversary to inject traffic that is ignored by a Tor client.
137
138 These remaining side channels are not as severe -- they cannot immediately be recognized by colluding relays using packet information alone. Instead the adversary must rely on packet volume and timing information in order to recognize the signal. However, if the volume of injected traffic is large enough or other conditions are right, [it may still be possible](https://petsymposium.org/2018/files/papers/issue2/popets-2018-0011.pdf) to use statistical methods to recover a signal.
139
140 The component uses
141[new control port features](https://trac.torproject.org/projects/tor/ticket/25903) and [improved connection tracking in Tor](https://trac.torproject.org/projects/tor/ticket/25573) to measure
142the quantity of traffic that Tor decides to drop from a circuit, to protect against
143[DropMark](https://petsymposium.org/2018/files/papers/issue2/popets-2018-0011.pdf)
144attacks.
145
146 The allowed dropped cell count is 0, and cannot be configured.
147
1482. ***Total Hidden Service Descriptor Kilobytes***
149
150 In addition to injecting relay cells that are dropped, it is also possible for relays to inject data at the end of an onion service descriptor, or in response to an onion service descriptor submission. Tor will continue reading this data prior to attempting to parse the descriptor or response, and these parsers can be convinced to discard additional data.
151
152 The bandguards subsystem sets a limit on the total amount of traffic allowed on onion service descriptor circuits (currently 30 kilobytes). Once this limit is exceeded, the circuit is closed and a WARN log message is emitted by the bandguards subsystem.
153
154 If your service uses OnionBalance, or has set a large number of custom
155introduction points, you may need to raise this limit via the
156**circ_max_hsdesc_kilobytes** setting in the [configuration
157file](https://github.com/mikeperry-tor/vanguards/blob/master/vanguards-example.conf).
158
1593. ***Total Circuit Megabytes***
160
161 A final vector for injecting side channel traffic is at the application layer.
162
163 If an attacker wants to introduce a side channel towards an onion service, they can fetch large quantities of data from that service, or make large HTTP posts towards the service, in order to generate detectable traffic patterns.
164
165 These traffic patterns can be detected in Tor's public relay bandwidth
166statistics, as well as via netflow connection volume records. The Tor Project
167is currently working on various mechanisms to reduce the granularity of these
168statistics (and has already reduced them to 24 hours of aggregate data), and
169has also deployed padding mechanisms to limit the resolution of netflow traffic
170logs, but it is not clear that these mechanisms are sufficient to obscure very
171large volumes of traffic.
172
173 Because of this, the bandguards subsystem has the ability to limit the
174total number of bytes sent over a circuit before a WARN is emitted and the
175circuit is closed. This limit is currently set to 0 (which means unlimited).
176If you know a reasonable bound for the amount of data your application or
177service should send on a circuit, be sure to set it to that value.
178
179 **If your service or application depends upon the ability of people to make
180very very large transfers (such as OnionShare, or a SecureDrop instance), you
181should keep this disabled, or at best, set it to multiple gigabytes.**
182
183 If your service is a normal website that does not transmit large content,
184100 megabytes is a reasonable value for this setting.
185
186 We believe that using two entry guards makes closing the circuit a
187worthwhile defense for applications where it is possible to use it. If the
188adversary is forced to split their side channel across multiple circuits, they
189won't necessarily know which guard node each circuit traversed. This should
190increase the quantity of data they must inject in order to successfully mount
191this attack (and by more than just a factor of two, because of this uncertainty).
192
193 Long-term, this feature is meant to be deployed in combination with
194[conflux traffic
195splitting](https://www.cypherpunks.ca/~iang/pubs/conflux-pets.pdf) so that we
196can tear down one path of a circuit after over-use without loss of
197connectivity, and reconnect the remaining portion to a new circuit.
198
199 If you wish to enable this defense, change the value of
200**circ_max_megabytes** in the [configuration file](https://github.com/mikeperry-tor/vanguards/blob/master/vanguards-example.conf).
201
2024. ***Max Circuit Age***
203
204 Since Tor currently rotates to new TLS connections every week, if a circuit stays open longer than this period, then it will cause its old TLS connection to be held open. After a while, the circuit will be one of the few things using that TLS connection. This lack of multiplexing makes traffic analysis easier.
205
206 For an example of an attack that makes use of this type of side channel, see [TorScan](https://eprint.iacr.org/2012/432.pdf). For additional discussion, see Tor Ticket [#22728](https://trac.torproject.org/projects/tor/ticket/22728) and [#23980](https://trac.torproject.org/projects/tor/ticket/23980).
207
208 For this reason, if your onion service does not require long-lived circuits, it is wise to close any that hang around for long enough to approach this rotation time.
209
210 The current default for maximum circuit age is 24 hours, and can be changed
211via **circ_max_age_hours** in the [configuration
212file](https://github.com/mikeperry-tor/vanguards/blob/master/vanguards-example.conf).
213
2145. ***Connectivity to the Tor Network***
215
216 Reachability itself is a side-channel. An adversary can correlate your
217uptime to other events to reduce your anonymity, or even actively attempt to
218influence connectivity to parts of the Tor network to determine if a specific
219service is using them. Because of this, we have added monitoring of connectivity
220to the Tor Network. The addon will alert you if all of your guard connections
221go down, or if you are unable to build circuits for a set amount of time.
222
223 Obviously, clients may want to disable this monitoring, especially if they
224are disconnected frequently. To disable these checks, change the
225***circ_max_disconnected_secs*** and ***conn_max_disconnected_secs***
226configuration settings to 0.
227
228# Security Information
229
230For additional security information, please see
231[README\_SECURITY.md](https://github.com/mikeperry-tor/vanguards/blob/master/README_SECURITY.md).
232
233
README_TESTS.md
1# How to run the tests
2
3This repository is configured to run unit tests on every commit in a pinned
4virtual environment via [Travis CI](https://travis-ci.org/mikeperry-tor/vanguards/).
5
6You can run the tests yourself with the python-tox and python-pytest packages,
7simply by running 'tox' in the root directory of this source tree. This will
8re-create the same test environment run on Travis CI, with the same pinned
9dependency versions.
10
11To use your distribution's packages instead, run:
12
13```
14 tox -c tox-systemonly.ini
15```
16
17or for each python version individually as:
18
19```
20 TOXENV=py2 tox -c tox-systemonly.ini
21 TOXENV=py3 tox -c tox-systemonly.ini
22 TOXENV=pypy tox -c tox-systemonly.ini
23```
24
25
26This will run python2, python3, and pypy tests, **as well as check your
27system-installed packages for known vulnerabilities against
28https://pyup.io/safety**.
29
30To run just the tests in the bare source tree against the git checkout in
31combination with system-wide packages, with no installation or known
32vulnerability checks, run:
33
34```
35 PYTHONPATH=src python2 -m pytest tests/
36 PYTHONPATH=src python3 -m pytest tests/
37 PYTHONPATH=src pypy -m pytest tests/
38```
39
40After system-wide installation of the vanguards package, you can run the tests
41without the PYTHONPATH specifier, to check the installed package:
42
43```
44 python2 -m pytest tests/
45 python3 -m pytest tests/
46 pypy -m pytest tests/
47```
48