1# What does this addon do? 2 3This addon uses the [Stem Tor control port 4library](https://stem.torproject.org/) to connect to a Tor control port 5listening on port 9051 (or on an alternate user-specified port, or UNIX file 6system socket). 7 8This addon protects against guard discovery and related traffic analysis 9attacks. A guard discovery attack enables an adversary to determine the guard 10node(s) that are in use by a Tor client and/or Tor onion service. Once the 11guard node is known, traffic analysis attacks that can deanonymize an onion 12service (or onion service user) become easier. 13 14The most basic form of this attack is to make many connections to a Tor onion 15service, in order to force it to create circuits until one of the adversary's 16relay is chosen for the middle hop next to the guard. That is possible because 17middle hops for rendezvous circuits are picked from the set of all relays: 18 19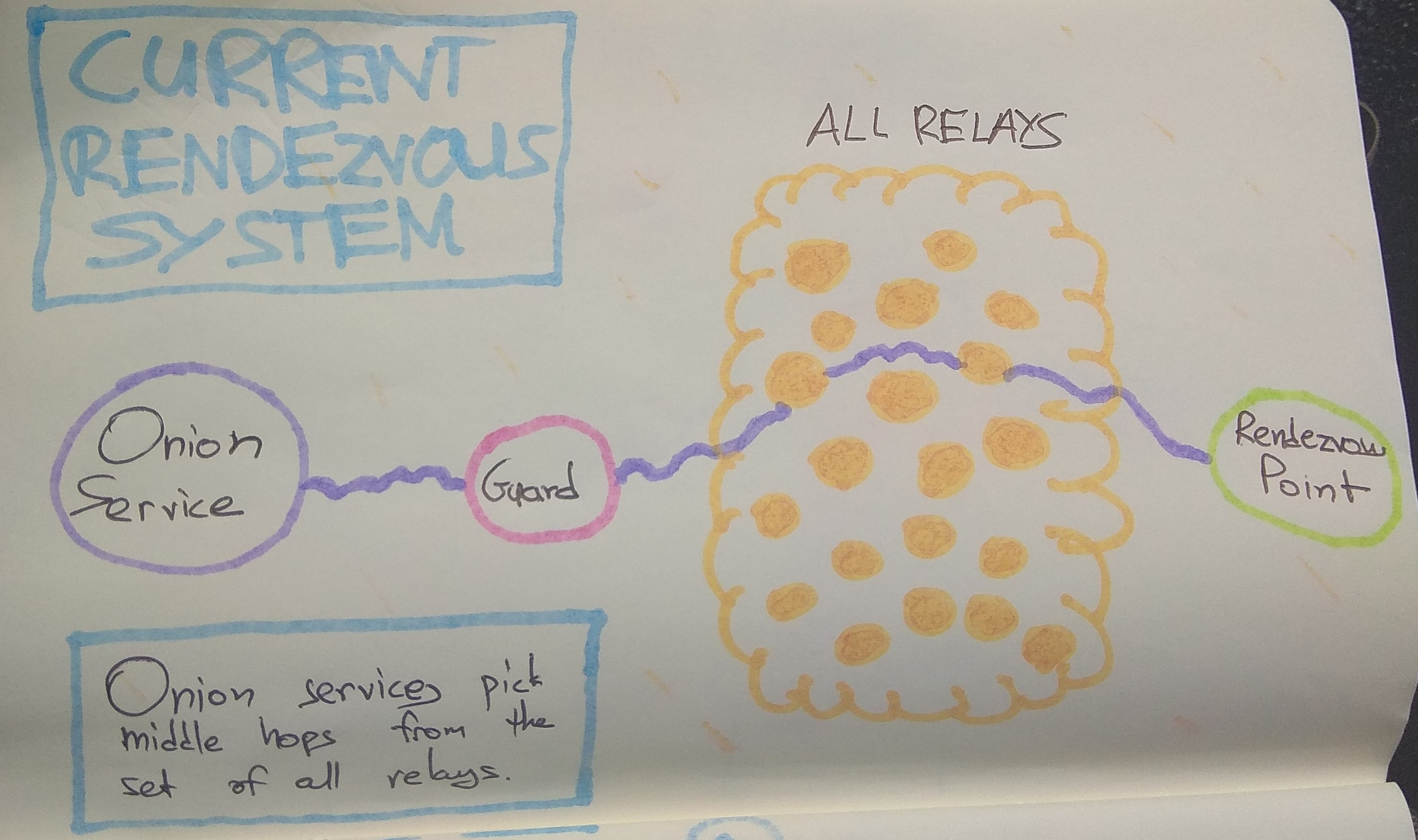 20 21This attack can also be performed against clients, by inducing them to create 22lots of connections to different onion services, by for example, injecting 23lots of onion-hosted images/elements into a page. 24 25A traffic analysis side channel can be used to confirm that the malicious node 26is in fact part of the rendezvous circuit, leading to the discovery of that 27onion service's or client's guard node. From that point, the guard node can be 28compromised, coerced, or surveilled to determine the actual IP address of the 29onion service or client. 30 31To defend against these attacks, this addon has three defense subsystems: 32Vanguards, Rendguard, and Bandguards. 33 34All three subsystems apply to both service-side and client-side onion service 35activity. With Tor v0.3.5.1 and Vanguards v0.3.0 and above, the Bandguards 36subsystem also applies to client traffic that exits the Tor network to the 37normal Internet. 38 39## The Vanguards Subsystem 40 41The Vanguards subsystem uses the [Tor control 42protocol](https://gitweb.torproject.org/torspec.git/tree/control-spec.txt) to 43select nodes from the Tor consensus for use with the torrc options HSLayer2Nodes 44and HSLayer3Nodes. 45 46Each of these options is assigned its own set of nodes, which are rotated 47based on the randomized selection algorithm specified in [the Mesh Vanguards 48Proposal](https://gitweb.torproject.org/torspec.git/tree/proposals/292-mesh-vanguards.txt). 49 50These options ensure that all onion service circuits are restricted to a set 51of second and third layer guards, instead of sampling random ones from the 52whole network every time. 53 54The change to fixed nodes for the second and third layer guards is designed 55to force the adversary to have to run many more nodes, and to execute both an 56active sybil attack, as well as a node compromise attack. In particular, the 57addition of second layer guard nodes means that the adversary goes from being 58able to discover your guard in minutes by running just one middle node, to 59requiring them to sustain the attack for weeks or even months, even if they 60run 5% of the network. 61 62The analysis behind our choice for the number of guards at each layer, and for 63rotation duration parameters is [available on 64GitHub](https://github.com/asn-d6/vanguard_simulator/wiki/Optimizing-vanguard-topologies). 65Here is how our current vanguard 2-3-8 topology looks like: 66 67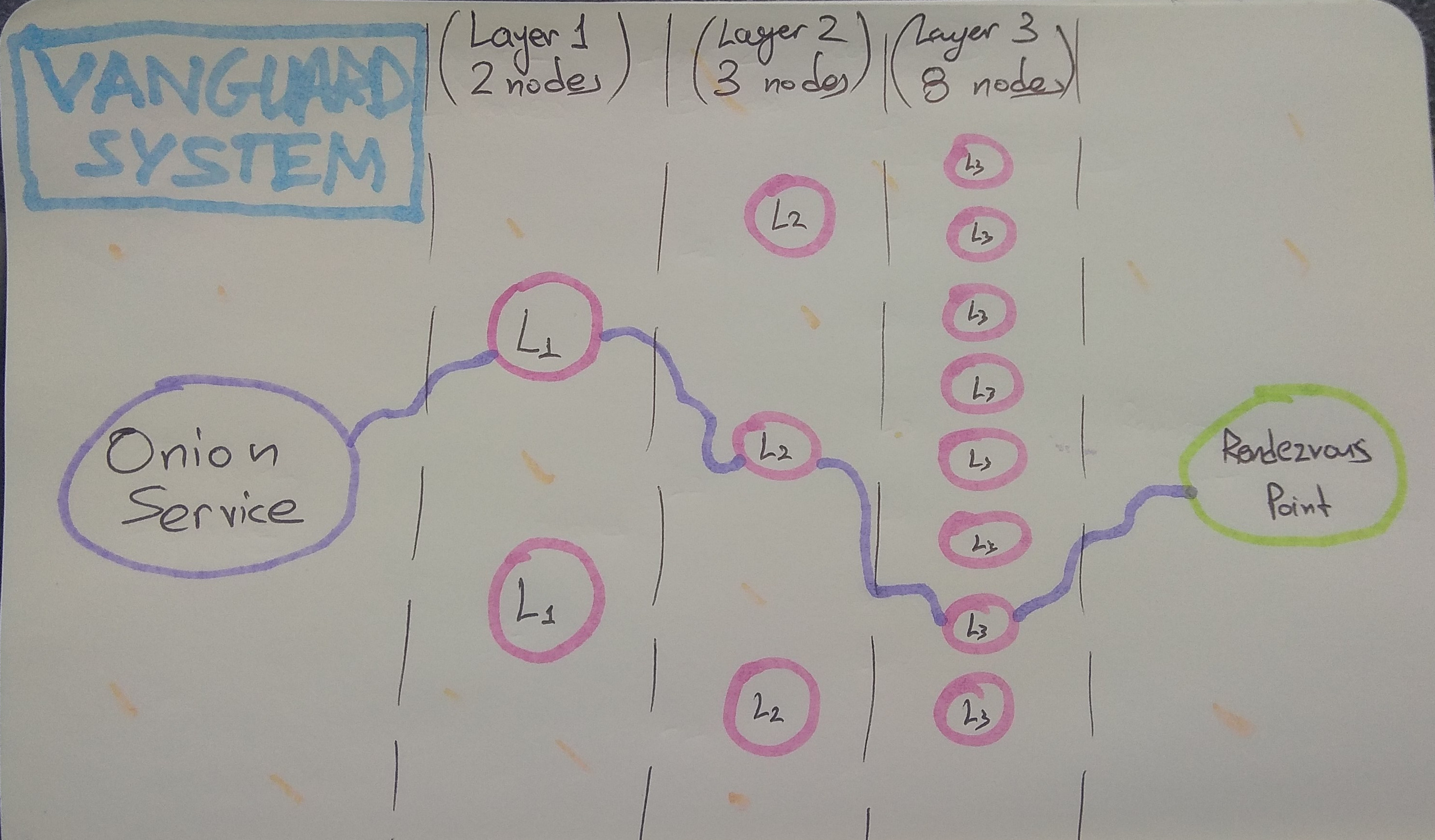 68 69Furthermore, to better protect the identity of these new pinned guard nodes, 70and to avoid linkability of activity, the circuit lengths have been 71altered for rendezvous point circuits, hidden service directory circuits, and 72introduction point circuits. You can see them here (where L1 is the first 73layer guard, L2 is second layer guard, L3 is third layer guard, M is random 74middle): 75 76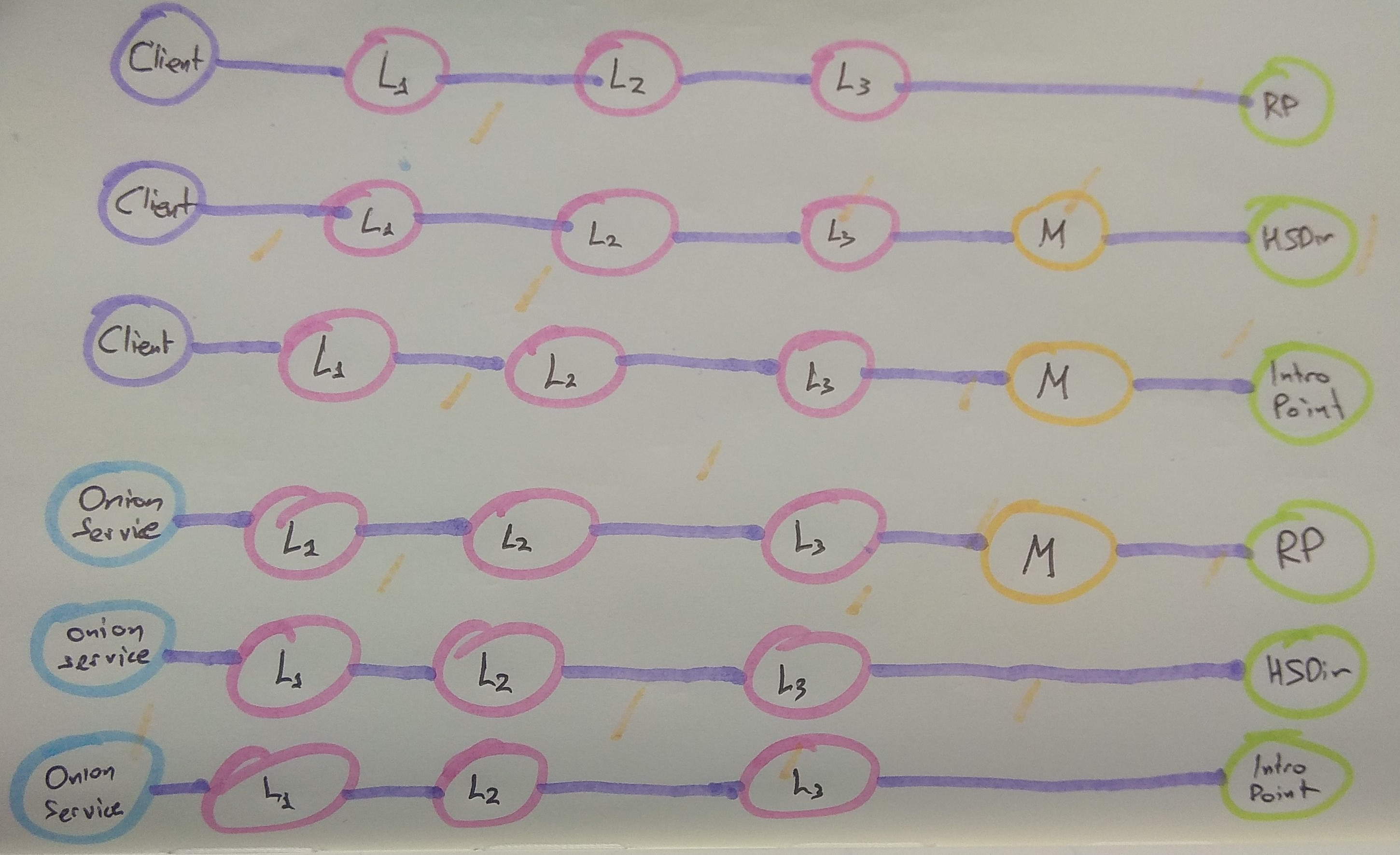 78 79The number of nodes in each of these sets, as well as the ranges on rotation 80times for each set, can be specified as config file parameters. The subsystem 81currently uses 2 entry guards, 3 layer2 guards, and 8 layer3 guards. 82 83High load onion services may consider using 4 layer2 guards by changing the 84**num_layer2_guards** option in the [configuration 85file](https://github.com/mikeperry-tor/vanguards/blob/master/vanguards-example.conf), but going beyond that is not recommended. 86 87## The Rendguard Subsystem 88 89The Rendguard subsystem keeps track of how often various relays appear in the 90rendezvous point position on the service side of an onion service. Since 91rendezvous points are chosen by the client that connects to a service, it 92is possible for clients to [choose malicious, colluding rendezvous 93points](https://www.ieee-security.org/TC/SP2013/papers/4977a080.pdf) to 94help them mount guard discovery and other attacks. 95 96This subsystem emits warnings and optionally closes the circuit when a 97rendezvous point is chosen too often compared to its consensus weight (the 98"too often" limit is set by the **rend_use_max_use_to_bw_ratio** config 99option, which defaults to 5X of a relay's consensus weight). 100 101We assign an aggregate weight of **rend_use_max_consensus_weight_churn** 102(default: 1% of consensus total) for relays that are not in our current 103consensus that are used as rendezvous points. It is valid to use relays that 104are not in the consensus as rendezvous points, and this can happen naturally 105when a client's consensus is from a different time period as the service's 106consensus. To prevent arbitrary computers from being used as rendezvous 107points, we set this bound on the maximum amount of consensus churn, and use 108that to limit all rendezvous requests that are not present in the service's 109consensus. 110 111When rendezvous points are overused and blocked by the addon, the effect is 112that clients get connection refused responses when they attempt to use 113rendezvous points that are already overused. Since the adversary gets to pick 114their rendezvous point, they can trigger these limits at will, and cause 115popular rendezvous points to be blocked by your service. If this happens, you 116can set **rend_use_close_circuits_on_overuse** to false in your configuration 117file. If you do this, rendezvous overuse messages will appear at WARN level, 118but circuits will not be closed. 119 120## The Bandguards Subsystem 121 122The bandguards subsystem performs accounting to watch for signs of bandwidth 123sidechannel attacks on individual onion service circuits as well as exit 124circuits. It then closes circuits that exceed these limits and emits log 125messages. While we expect the default values to be set properly, these limits 126can be tuned through configuration as well. See the [configuration 127file](https://github.com/mikeperry-tor/vanguards/blob/master/vanguards-example.conf) 128for more details. 129 130These limits (along with a reason for checking them) are as follows: 131 1321. ***Dropped Cell Limit*** 133 134 Back in 2014, the Tor network [was attacked](https://blog.torproject.org/tor-security-advisory-relay-early-traffic-confirmation-attack) by Carnegie Mellon researchers ([likely on behalf of the FBI)](https://blog.torproject.org/did-fbi-pay-university-attack-tor-users). The attack injected a side channel using a special packet type that could be recognized at both ends of a Tor circuit. 135 136 This side channel was fixed. Unfortunately, there are many other side channels available that allow an adversary to inject traffic that is ignored by a Tor client. 137 138 These remaining side channels are not as severe -- they cannot immediately be recognized by colluding relays using packet information alone. Instead the adversary must rely on packet volume and timing information in order to recognize the signal. However, if the volume of injected traffic is large enough or other conditions are right, [it may still be possible](https://petsymposium.org/2018/files/papers/issue2/popets-2018-0011.pdf) to use statistical methods to recover a signal. 139 140 The component uses 141[new control port features](https://trac.torproject.org/projects/tor/ticket/25903) and [improved connection tracking in Tor](https://trac.torproject.org/projects/tor/ticket/25573) to measure 142the quantity of traffic that Tor decides to drop from a circuit, to protect against 143[DropMark](https://petsymposium.org/2018/files/papers/issue2/popets-2018-0011.pdf) 144attacks. 145 146 The allowed dropped cell count is 0, and cannot be configured. 147 1482. ***Total Hidden Service Descriptor Kilobytes*** 149 150 In addition to injecting relay cells that are dropped, it is also possible for relays to inject data at the end of an onion service descriptor, or in response to an onion service descriptor submission. Tor will continue reading this data prior to attempting to parse the descriptor or response, and these parsers can be convinced to discard additional data. 151 152 The bandguards subsystem sets a limit on the total amount of traffic allowed on onion service descriptor circuits (currently 30 kilobytes). Once this limit is exceeded, the circuit is closed and a WARN log message is emitted by the bandguards subsystem. 153 154 If your service uses OnionBalance, or has set a large number of custom 155introduction points, you may need to raise this limit via the 156**circ_max_hsdesc_kilobytes** setting in the [configuration 157file](https://github.com/mikeperry-tor/vanguards/blob/master/vanguards-example.conf). 158 1593. ***Total Circuit Megabytes*** 160 161 A final vector for injecting side channel traffic is at the application layer. 162 163 If an attacker wants to introduce a side channel towards an onion service, they can fetch large quantities of data from that service, or make large HTTP posts towards the service, in order to generate detectable traffic patterns. 164 165 These traffic patterns can be detected in Tor's public relay bandwidth 166statistics, as well as via netflow connection volume records. The Tor Project 167is currently working on various mechanisms to reduce the granularity of these 168statistics (and has already reduced them to 24 hours of aggregate data), and 169has also deployed padding mechanisms to limit the resolution of netflow traffic 170logs, but it is not clear that these mechanisms are sufficient to obscure very 171large volumes of traffic. 172 173 Because of this, the bandguards subsystem has the ability to limit the 174total number of bytes sent over a circuit before a WARN is emitted and the 175circuit is closed. This limit is currently set to 0 (which means unlimited). 176If you know a reasonable bound for the amount of data your application or 177service should send on a circuit, be sure to set it to that value. 178 179 **If your service or application depends upon the ability of people to make 180very very large transfers (such as OnionShare, or a SecureDrop instance), you 181should keep this disabled, or at best, set it to multiple gigabytes.** 182 183 If your service is a normal website that does not transmit large content, 184100 megabytes is a reasonable value for this setting. 185 186 We believe that using two entry guards makes closing the circuit a 187worthwhile defense for applications where it is possible to use it. If the 188adversary is forced to split their side channel across multiple circuits, they 189won't necessarily know which guard node each circuit traversed. This should 190increase the quantity of data they must inject in order to successfully mount 191this attack (and by more than just a factor of two, because of this uncertainty). 192 193 Long-term, this feature is meant to be deployed in combination with 194[conflux traffic 195splitting](https://www.cypherpunks.ca/~iang/pubs/conflux-pets.pdf) so that we 196can tear down one path of a circuit after over-use without loss of 197connectivity, and reconnect the remaining portion to a new circuit. 198 199 If you wish to enable this defense, change the value of 200**circ_max_megabytes** in the [configuration file](https://github.com/mikeperry-tor/vanguards/blob/master/vanguards-example.conf). 201 2024. ***Max Circuit Age*** 203 204 Since Tor currently rotates to new TLS connections every week, if a circuit stays open longer than this period, then it will cause its old TLS connection to be held open. After a while, the circuit will be one of the few things using that TLS connection. This lack of multiplexing makes traffic analysis easier. 205 206 For an example of an attack that makes use of this type of side channel, see [TorScan](https://eprint.iacr.org/2012/432.pdf). For additional discussion, see Tor Ticket [#22728](https://trac.torproject.org/projects/tor/ticket/22728) and [#23980](https://trac.torproject.org/projects/tor/ticket/23980). 207 208 For this reason, if your onion service does not require long-lived circuits, it is wise to close any that hang around for long enough to approach this rotation time. 209 210 The current default for maximum circuit age is 24 hours, and can be changed 211via **circ_max_age_hours** in the [configuration 212file](https://github.com/mikeperry-tor/vanguards/blob/master/vanguards-example.conf). 213 2145. ***Connectivity to the Tor Network*** 215 216 Reachability itself is a side-channel. An adversary can correlate your 217uptime to other events to reduce your anonymity, or even actively attempt to 218influence connectivity to parts of the Tor network to determine if a specific 219service is using them. Because of this, we have added monitoring of connectivity 220to the Tor Network. The addon will alert you if all of your guard connections 221go down, or if you are unable to build circuits for a set amount of time. 222 223 Obviously, clients may want to disable this monitoring, especially if they 224are disconnected frequently. To disable these checks, change the 225***circ_max_disconnected_secs*** and ***conn_max_disconnected_secs*** 226configuration settings to 0. 227 228# Security Information 229 230For additional security information, please see 231[README\_SECURITY.md](https://github.com/mikeperry-tor/vanguards/blob/master/README_SECURITY.md). 232 233